TUCTF 2019
Contents
I tried TU CTF.
I only played 1 or 2 hours and flagged quite a lot: this is an easy CTF, good for beginners. See some very quick write-ups below.
Unfortunately I can’t remember the titles of the challenges.
Challenge 1
We have a binary to decompile. I use Ghidra and locate a strange function called thisone
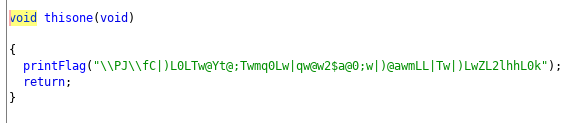
The printFlag function decodes the flag.
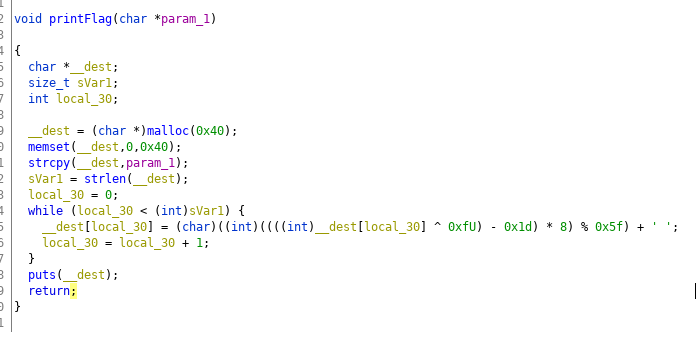
I write a program to mimic the decoding:
| |
I get the flag: TUCTF{7h3r35_4lw4y5_m0r3_70_4_b1n4ry_7h4n_m3375_7h3_d3bu663r}
Challenge 2
We got an object file run.o. We decompile it using Ghidra.
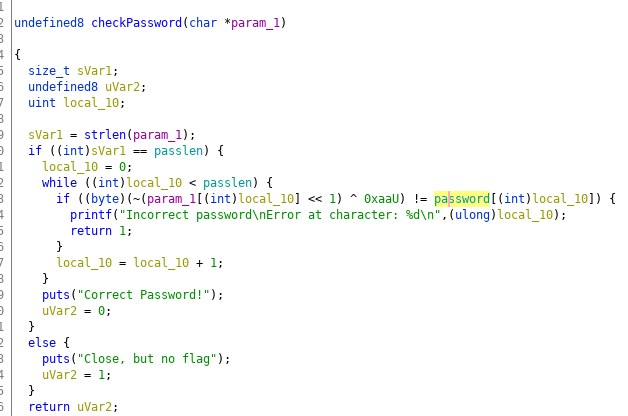
The function checkPassword explains how the password is validated. There is an XOR with 0xaa.
I write the following code:
| |
and get the flag: TUCTF{c0n6r47ul4710n5_0n_br34k1n6_7h15_fl46}