BruCON 2023 CTF Critical Infrastructure Challenges
This is a write-up for some of the PLC / Critical Infrastructure challenges of BruCON.
PLC: The Secret Ingredient
This is an OT challenge where we interact with a real PLC. We are asked to “get the PLC program and rescue the company secret located in datablock 23”. The IP address of the PLC is 35.232.66.239:102.
I solved this one with a team mate, and he did the most difficult part. This challenge was only worth 50 points in the end, I think it should have earned us more.
The PLC is a S7-300:
| |
On the web, I found several exploits from Beresford, 2011 which basically consisted in commanding several START and STOP of the PLC, and another one to dump the PLC’s memory. I tried those scripts on metasploit but they wouldn’t work (implementation error - probably no longer compatible with recent languages).
My team mate found a Python library, snap7, to discuss with the PLC. The rack and slot depend on the PLC’s model (here for a S7-300). The datablock number was provided in the description.
| |
When we run this program, we get the following answer:
| |
The description was asking for a UUID as flag, but that was an error. I could have searched for a long time, fortunately I tried “CRIMINAL_HOPS” by pure luck and that was the flag. The organizers explained that in other CTFs they were asking for the UUID and that this was an error.
PLC: Rerouting the brew
In this second PLC challenge, we are now asked: “Manipulate the outlow of the pressure tank by setting the PLC outputs 2,4 and 6. Verify the changes by verifying the datablock 42.”.
Same the solution below is mostly the work of a team mate.
| |
CTI
Those were several challenges on Critical Infrastructure. For all of them, we had a common pcap and smbp file
CTI: Find the PDF
This challenge asked “Find the PDF document file name within the network packet capture”.
We didn’t even need to load the Pcap in Wireshark. Mere strings on the pcap and grepping on pdf revealed the name of the PDF. The flag was the name of the PDF.
| |
CTI: Which subnet
“Which subnet from the enterprise domain network exfiltrates the PDF document?”
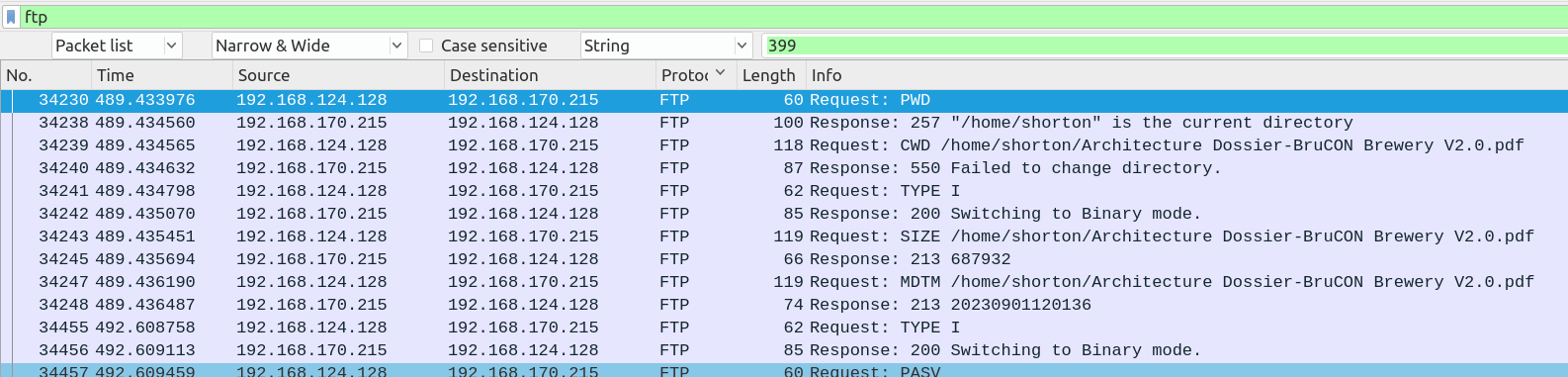
IP address 192.168.124.128 is getting the PDF via FTP. The FTP server is 192.168.170.215. We struggled a long time on this one, because we thought we had to supply 192.168.0.0/16 as answer, and it did not work.
In the end, I asked an organizer who made me understand he wasn’t expecting a technical representation of the subnet but it’s name in the network architecture diagram. This diagram was supplied in a PDF for the CTI Architecture challenges.

We see the PDF is exfiltrated from a workstation in the Marketing subnet. Marketing was the flag.
CTI: Devices
“How many devices did communicate with the PLC”
Devices who communicate with a PLC use the ModBus protocol. We can filter such packets in Wireshark with the filter “mdtcp” (or we could have filtered communications to the PLC’s IP address).
In ModBus we have communications between 192.168.174.242 and
- 192.168.170.240 (SCADA)
- 192.168.174.99 (PLC)
- 192.168.174.245 (PLC)
To be honest, when I flagged I hadn’t understood this at all, and tried 1, then 2 and happily got the flag with answer 3…
CTI: Mac Addy
“What is the MAC address of the PLC?”
I solved this one by looking at the file GRC_known_good.smbp first. It’s an XML file and we see this IP address:
| |
So, then I looked for 192.168.174.242 in Wireshark and found its MAC address: 00:80:f4:0e:8d:13. This was the flag.
CTI Architecture
For those challenges, we were given a 9-page PDF titled “BruCON Brewery Architecture Dossier”. PDF.
The point of all challenges in this section was to read this PDF and comment it on a security point of view. The issue is that the expected answers weren’t technical ones like “an attacker can send a phishing email to crab the credentials of an employee” but high level concepts.
The first question consisted in commenting what was mainly missing in the network diagram. Basically, the issue was that there was no firewall to secure the traffic inside the company between subnets. The expected answer was something like “micro segmentation”, “IEC64443” and “Purdue Model”.
There was a question on flaws of the logging system. The first issue I saw was that it would be possible to erase logs. The solution they expected was how to solve it, such as duplicating the logs, if possible in another branch of the company physically located elsewhere.
There were also questions about remote access of employees and issues with how it was designed. A first flag came by saying that whitelisting IP addresses was insufficient to guarantee the connection came from an employee and that 2FA could be a solution to partly remedy the issue. Another flag came by arguing that there was no VPN from the employee’s location to the enterprise. Discussed about the fact that employees were actually not authentified and that the enterprise has no real idea who they were, just that they were authorized or not, and that the inner RBAC strategy should have been deployed also externally.
While those challenges were interesting, I regret that the solution was too much to talk your way out to get the flag. I would have preferred a very strictly formatted flag based on more precise questions. But overall, the idea of studying the PDF was excellent.